
The author(s) shown below used Federal funding provided by the U.S.
Department of Justice to prepare the following resource:
Document Title: Exploring Elder Financial Exploitation
Victimization: Identifying Unique Risk
Profiles and Factors to Enhance Detection,
Prevention and Intervention
Author(s): Jason Burnett, Ph.D., Rui Xia, Ph.D., Robert
Suchting, Ph.D., Carmel B. Dyer, Ph.D.
Document Number: 250756
Date Received: May 2017
Award Number: 2013-IJ-CX-0050
This resource has not been published by the U.S. Department of
Justice. This resource is being made publically available through the
Office of Justice Programs’ National Criminal Justice Reference
Service.
Opinions or points of view expressed are those of the author(s) and
do not necessarily reflect the official position or policies of the U.S.
Department of Justice.
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
National Institute of Justice Final Technical Report
Exploring Elder Financial Exploitation Victimization: Identifying Unique Risk Profiles and
Factors to Enhance Detection, Prevention and Intervention
Grant # 2013-IJ-CX-0050
1
Jason Burnett, PhD,
1
Rui Xia, PhD,
2
Robert Suchting, PhD and
1
Carmel B. Dyer, PhD
Affiliations:
1
The University of Texas Health Science Center at Houston, UTHealth, McGovern Medical
School, Division of Geriatric and Palliative Medicine
2
The University of Texas Health Science Center at Houston, UTHealth, McGovern Medical
School, Department of Psychiatry and Behavioral Sciences
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
The authors are currently preparing a manuscript, describing the primary findings, which will be
submitted to the American Journal of Public Health. Other peer-reviewed journals of interest for
further dissemination of relevant findings such as understanding the association between FE
types and recidivism and different combinations of FE include the Journal of the American
Geriatrics Society, the Gerontologist and Psychology of Violence.
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
National Institute of Justice Final Technical Report
Exploring Elder Financial Exploitation Victimization: Identifying Unique Risk Profiles and
Factors to Enhance Detection, Prevention and Intervention
Grant # 2013-IJ-CX-0050
Abstract
Statement of Purpose: Explore risk factors across the socioecological framework (i.e. individual,
perpetrator and community-levels) to identify the most important factors that differentiate elder
financial exploitation (FE) from other forms of abuse as well as pure FE from hybrid FE.
Description of Research Subjects: Older adults 65 years and older with a confirmed case of abuse
(i.e. financial exploitation, caregiver neglect, physical abuse, emotional abuse) by Texas Adult
Protective Services between the years 2009 – 2014. Methods: Secondary data analysis of a 5-
year statewide aggregated cohort of Texas Adult Protective Services confirmed cases of abuse
between the years 2009 – 2014. Case investigation data such as demographics, reported and
confirmed abuse types, victim and perpetrator mental and physical health, substance use, social
and financial factors along with community-level data (Geographic Information Systems) were
analyzed. Supervised Learning, which provides a step-by-step statistical decision-making process
was used to identify the most reliable, interpretive and predictive risk factor models. Training and
test sampling was included for replication purposes. Results: Financially-based variables are the
best predictors of FE versus other forms of abuse, but apparent injury appears to be the most
important indicator of other forms of abuse even in the presence of FE. Hybrid FE may be strongly
related to poorer outcomes compared to pure FE however, the most predictive model found
negative effects of others, alcohol and substance use by others as well as foreclosure and
inadequate medical supplies to be the most important predictors of hybrid FE. Models that
accounted for less linearity between the variables resulted in greater accuracy in group
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
classification indicating the need to account for complex interactions across the socioecological
context. Conclusion: Different factors across the socioecological context are needed to reliably
differentiate between elder FE and other forms of abuse as well as pure versus hybrid FE. These
factors will also vary depending on the perspective one takes regarding the linearity of the
interactions between the different factors. The findings provide support for the need to differentiate
between types of abuse and subtypes of elder FE and the need for frontline workers and social
service agencies and researchers to account for variables across the socioecological context when
developing surveillance, intervention and prevention programs.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Executive Summary
Financial exploitation (FE) in older adults is the “illegal taking, misuse or concealment of
funds, property or assets of a vulnerable elder” (National Center on Elder Abuse:
https://ncea.acl.gov/faq/index.html#faq1) and poses a serious public health problem. In two US
national prevalence studies, FE represented the highest percent (5.2%) of self-reported abuse
among cognitively intact community-dwelling older adults (Acierno et al., 2010) and occurred in
21% of all cases reported to Adult Protective Services (APS) (Teaster et al., 2006). The estimated
financial loss among older Americans in 2012, as a result of FE, was 2.9 billion (MetLife, 2012).
Other outcomes include financial ruin (Dessin, 2000), loss of independence and security (Choi et
al., 1999), decline in quality of life (Coker, 1997), decreased resources for health care (Kemp et
al., 2005), depression and suicide (Nerenberg, 2000; Podneiks, 1992), emergency room visits and
hospital admissions (Dong et al, 2013; Dong et al., 2013) and increased risk of 5-year all-cause
mortality (Burnett et al., 2016).
Individual studies have found that victim characteristics associated with increased risk of
FE include impaired activities of daily living and dependence on others for care, (Peterson et al,
2014; Acierno et al., 2010; Amstadter et al., 2011), not having a spouse (Laumann et al., 2008)
reporting poor self-rated health (Amstadter et al., 2011) and non-use of social services (Acierno et
al., 2010). Culturally and ethnically relevant victim characteristics such as being African-
American or Non-White (Peterson et al., 2014; Amstadter et al., 2011; Laumann et al. 2008) have
also been linked to higher risks. Highly probable perpetrators commonly depend on the older adult
for finances (Hafemeister, 2003), abuse substances (Anetzberger, 1994) and are chronically
unemployed (Jackson and Hafemeister, 2012). Likewise, increasing the number of non-spousal
household members, living below the poverty threshold, and perceiving social support to be low
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
(Peterson et al., 2014; Amstadter et al., 2011) also appear to be associated with increased incidents
of FE victimization.
Adding complexity, recent evidence by Jackson and Hafemeister, (2012) suggests that FE
should be considered a construct with two unique subtypes (i.e. Hybrid FE and Pure FE). Hybrid
FE consists of FE victimization plus physical abuse and/or neglect and was associated with higher
percentages of victims reporting fair/poor health and fear of the abuser. The perpetrators were also
more likely to be a relative, chronically unemployed and financially dependent on the older adult.
Cohabitation and change in living arrangement from living alone to living with the perpetrator
were also associated with HFE versus Pure FE (i.e. no other forms of abuse or neglect). Moreover,
HFE victims suffered abuse longer and experienced a 2-fold higher financial loss over the course
of the victimization.
These studies provide evidence that factors associated with incidents of FE cut across multiple
levels of the socio-ecological context and that unique sets of factors are associated more so with
specific subtypes of FE. These findings could have important implications for intervention and
prevention programs. These efforts could be further facilitated by attempting to understand the
interactions between variables within and across the socioecological context that influence the risk
for FE or a specific subtype of FE. Because these interactions are not always linear and instead are
likely highly complex and require a tremendous amount of statistical computation, it is often
difficult to identify replicable models for identifying and classifying events as multifaceted as elder
abuse and FE victimization. Modeling the complexity of the interactions within large datasets can
be cumbersome and poses data analytic challenges based on sample size, variable load and the
ways in which the variables work together to influence the risk of an outcome. Nevertheless, large
APS derived datasets provide good sources of case relevant data regarding victim, perpetrator and
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
environmental characteristics and good opportunity for using commonly collected socio-
ecological data to determine which factors together can be used to most accurately classify victims
of elder FE victimization. Utilizing sophisticated analytic approaches designed to handle such
large datasets and complex variable interactions across multiple levels could move corroborate and
move the field beyond what has been learned from previous risk factor model building strategies
for both FE and its subtypes and provide evidence supporting the use of socio-ecological models
when studying elder FE.
Building upon the previous elder FE work, the current study utilizes five years of statewide
APS confirmed abuse cases to identify variables of highest importance across the socio-ecological
model for accurately distinguishing and classifying elder maltreatment victims as 1): FE versus
other forms of abuse and 2): Pure FE vs Hybrid FE. Findings from multiple analytic models
varying from the most interpretive to the most predictive will be reported to address these aims.
Implications for using a socio-ecological perspective to study elder FE victimization and its
subtypes as well as the utility of supervised learning algorithms to improve public health FE victim
surveillance and prevention will be discussed.
Methods
Sample
APS are state agencies charged with investigating reports of abuse, neglect and exploitation
in adults 18 years of age and older. These agencies perform investigations that include in-depth
data collection capturing victim, perpetrator and environmental details needed to substantiate or
fail to substantiate an allegation of abuse, neglect and/or exploitation. The data used to conduct
this secondary analysis were obtained from the Texas Department of Family and Protective
Services, Division of Adult Protective Services (APS). The data provided by APS for the current
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
study represent Texas statewide confirmed cases of elder abuse within the years of 2009 – 2014.
Only records for adults 65 years and older were included. The confirmed abuse types included
financial exploitation, physical abuse, emotional/verbal abuse (i.e. psychological abuse) and
caregiver neglect. Caregiver neglect consisted of any of the physical, medical and mental health
neglects where a perpetrator, other than the victim, was identified and confirmed.
Definitions of Abuse
The Texas Human Resource code Section 48.002 [a] defines the different types of elder
abuse investigated by Texas APS (Texas Department of Family and Protective Services, May
2010). For purposes of this study, these include: (a) emotional/verbal abuse—“any use of verbal
communication or other behavior to humiliate, intimidate, vilify, degrade, or threaten harm”; (b)
physical abuse —“abuse with resulting physical or emotional harm or pain to an elderly person
or adult with a disability by the person’s caretaker, family member, or other individual who has an
ongoing relationship with the person”; (c) caregiver neglect—“the failure of a caretaker to provide
the goods and/or services, including medical, physical or mental health to meet the needs of the
older adult” (d) financial exploitation—“the illegal or improper act or process of a caretaker,
family member, or other individual who has an ongoing relationship with a person age 65 or older
or an adult with a disability.”
Given the specific aims of this study and because FE can co-occur with other forms of
abuse, we chose to define FE in three ways: 1) FE with or without other forms of abuse, 2) Pure
FE –only confirmed FE and no other confirmed forms of abuse and 3) FE with other confirmed
forms of abuse.
Demographic Characteristics
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
As part of the APS assessment, standard demographic variables were collected for both the
alleged victims and perpetrators, when necessary. These variables include age, race/ethnicity,
gender and living status. Race/ethnicity classification followed the coding provided by the United
States Department of Health and Human Services. Other descriptive characteristics, including, but
not limited to cognitive status, mobility, drug abuse and hearing impairments were included. A
full list of these additional descriptive variables which are collected and recorded during the APS
investigation in conjunction with the Client Assessment and Risk Evaluation variables are included
in Appendix A.
Risk Assessment and Contextual Variables
All Texas APS referred cases of elder abuse receive an in-home investigation by an APS
caseworker. These investigations include a comprehensive risk assessment guided by the Client
Assessment and Risk Evaluation (CARE) tool. The CARE tool is used in conjunction with
ancillary data assessment questions to help confirm elder abuse incidents. This tool was initially
developed by the Texas Department of Family and Regulatory Services, Division of Adult
Protective Services and the Texas Health and Human Services to improve the assessment and
service delivery process for cases of mistreatment and self-neglect. Each APS caseworker receives
extensive field and manual based training (i.e. 6 weeks) on how to properly administer and record
data using the CARE tool. The CARE tool demonstrated efficiency and comprehensiveness when
field tested on adults 60 years of age and older.
The CARE tool consists of 57 items assessing the presence and absence of risks for harm
associated with the different types of elder mistreatment (i.e. verbal abuse, physical abuse,
psychological abuse, financial exploitation etc.) and self-neglect. These items are clustered in into
5 broad categories (i.e. living conditions, financial status, physical/medical status, mental status,
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
social interaction) with 15 subcategories. The subcategories contain different risk indicators
related to the different types of elder mistreatment and self-neglect. Each risk indicator follows an
ordinal scale of measurement with the available response options of no problem, managed risk,
problem, severe problem, not applicable and unable to determine. Each level of risk has a
descriptive phrase to help the assessor decide on its appropriateness for the given client. A
validated allegation is indicated by the identification of a problem or severe problem in any
category.
A recent study conducted by Burnett et al. (2014) investigated the construct validity and
measurement invariance of the CARE tool. The findings validated the 5-factor structural model,
but resulted in the removal of 14 items. The new 5-factor model was cross-validated on a randomly
allocated hold-out sample and also showed adequate factor and item-threshold invariance across
gender and ethnicity. Because the CARE tool was only validated using data from one region in
Texas, the full CARE tool was utilized in this study. The CARE tool can be found in Appendix B.
U.S Census Data and Geographic Information Systems
The US Census Data for the years 2009 – 2014 were used in conjunction with Geographic
Information Systems to identify community-level risk and protective factors associated with elder
FE. Some of the community-level variables to be assessed are located in Appendix A. Geographic
information systems (GIS) are computer systems designed to collect, manage, manipulate, overlay,
analyze, and visualize spatial and non-spatial data (Steinberg & Steinberg, 2007). GIS makes it
possible to link personal attributes or circumstances (e.g. health, demographic information, and
financial exploitation) with features situated in space, which can then be analyzed for spatial
patterns or graphed on a map. Public health researchers have used GIS to gain a better
understanding of how environmental factors contribute to specific diseases and outcomes as well
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
as to develop targeted service plans. However, to date, GIS remains underutilized in the literature
(Hirshorn & Stewart, 2003) and to the best of our knowledge, few studies have utilized GIS as a
tool to study the issue of elder abuse and specifically, FE (e.g. Payne & Gainey, 2009) despite its
evidence-based use in examining patterns of child mistreatment (Ernst, 2000). A list of these
variables can be found in Appendix A.
Analytic Strategy
Standard data cleaning techniques described by Tabachnick and Fidell (2001) were used
to review the data for missing variables and values as well as out of range values based on each
variable. Missing data were assessed and in instances where missingness accounted for more than
10% and a sensitivity analysis was conducted to permit evaluation of the robustness of findings to
missing data assumptions. These cleaning methods resulted in a final dataset used for subsequent
analyses.
Data Mining Overview
The present study used data mining to examine financial elder abuse. Data mining is a
broad term for the process of detecting previously unknown patterns from data (Witten, Frank, &
Hall, 2011). Other related (and sometimes interchangeable) words for data mining include machine
learning and statistical learning (Hastie, Tibshirani, & Friedman, 2009). Data mining algorithms
are used for prediction and knowledge discovery (insight into relationships underlying data). There
are myriad different algorithms for use in data mining, and no one algorithm is best for every data
set (e.g., James, Witten, Hastie, & Tibshirani, 2013). Further, algorithms vary in their levels of
interpretability and raw predictive power; that is, given a set of raw input, some algorithms may
provide excellent predictive performance through “black box,” opaque inner workings.
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Generally speaking, data mining algorithms work by tuning on a “training” set of data and
predicting outcomes on a “test” set of data. Optimally, these data sets are collected independently.
However, in practical situations, researchers often have one data set that must be split into sections
for training and testing. Several different methods for data splitting have been proposed and used
for data mining (for a review, see Kuhn & Johnson, 2013). The present study uses a two-way
random split for training and testing of 80% and 20%, respectively, stratified by a binary outcome
to ensure adequate representation of both categories in both splits. Of key importance is that after
splitting, the test set is completely held out and never used for training.
There are three major types of data mining algorithms: classification, regression, and
clustering. Classification and regression algorithms are considered “supervised learning” in that
they attempt to predict observations on an outcome variable of interest; the difference is that
classification examines categorical or binary outcomes, while regression investigates continuous
outcomes. Clustering algorithms are considered “unsupervised learning” where instead of
predicting an outcome, the algorithms seek to find underlying structure within the data. The present
study will focus on classification, as the outcome in question (elder abuse type) is categorical.
Many data mining algorithms, including those used in the present study, feature
hyperparameters: algorithmic constants that work as tuning knobs, whereby several different
values are tested to optimize performance. For example, in penalized regression, the magnitude of
shrinkage is governed by a hyperparameter that ranges between 0 and 1 called lambda; the closer
this value is to zero, the more a model resembles traditional ordinary least squares (OLS)
regression (e.g, at lambda = 0, there is no shrinkage).
Model tuning, including hyperparameter optimization, requires resampling procedures
within the training set. This may be accomplished in several ways (Kuhn & Johnson, 2013); in the
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
present study, this was realized using a technique called 10-fold cross-validation. This procedure
involves a ten-way split of the data, whereby 9/10 of the data and 1/10 of the data are selected in
turns to serve as sub-training and sub-test sets. Using this procedure, we can minimize the variance
in prediction (i.e., reduce the probability of poorly tuned algorithms that may result from
lucky/unlucky splits of the data).
In the present study, hyperparameters were tuned by randomly searching a grid space of
potential hyperparameter values, testing different values, and choosing the best fitting algorithm
of each type based on a scoring criteria. Several scoring criteria are typically available for this
purpose; here, the squared difference between predicted and observed values (mean squared error;
MSE) is used.
Data Mining
The present study used the open-source software H2O (Aiello, Kraljevic, & Maj, 2016)
scripted in the R statistical computing environment (R Core Team, 2016) and implemented in Java
to compare the performance of four data mining/machine learning algorithms in classifying
different types of elder abuse. H2O provided excellent tools for addressing the research problem:
cutting-edge implementations of some of the most powerful algorithms (generalized linear
modeling, random forests, gradient boosting machines, and deep learning), parallel processing
capabilities to optimize computational resources, and the capacity to scale for use in small and
large datasets alike, including “big” datasets (here, the present data included more than 150,000
observations).
Elder abuse in the present study comprised four categorizations: pure financial abuse,
hybrid financial abuse, other abuse, and no confirmed abuse. These categories were re-classified
into pairs for separate analyses to address specific research questions as follows:
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
(1) Given that we have evidence of abuse, can we discriminate between other confirmed
abuse (i.e. physical, caregiver and psychological) and financial exploitation?
(2) Given that we have evidence of financial exploitation, can we differentiate between
confirmed pure FE and confirmed hybrid FE?
This sequential questioning process was developed for two reasons. First, in a practical
sense, many machine learning algorithms are not well-equipped for classification with more than
two categories. The present approach affords the flexibility to use a wider range of algorithms
while simultaneously fine-tuning our exploration of the data. Second, the process mirrors the
manner in which an investigator may approach a novel instance of potential financial elder abuse
in the field: they would first assess the probability of any elder abuse, then proceed to discern
evidence for financial abuse, and finally determine whether that abuse was purely financial or
multi-faceted.
Data mining in the present study utilized four algorithms: penalized generalized linear
modeling, random forest, gradient boosting machines, and deep learning. Details of each algorithm
follow. Missing data on continuous predictors was handled natively within each algorithm;
however, categorical missingness was addressed by creating a unique category for each variable
that encapsulated all of the missing observations.
Generalized Linear Modeling (GLM). The most general form of a linear model, GLMs
can be considered a type of data mining algorithm in their ability to predict an outcome using a set
of inputs (predictors). The most basic form of a GLM is simple linear regression with one predictor
and one normally-distributed outcome; however, the model may be extended to situations with
many predictors and non-Gaussian outcomes, as in logistic regression.
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
The GLM as implemented in H2O (Nykodym, Kraljevic, Hussami, Rao, & Wang, 2016)
is further extended to include regularization in the form of an elastic net, a type of shrinkage and
variable selection penalty that mixes ridge regression and the lasso (Hastie, Tibshirani, &
Friedman, 2009). The elastic net requires two hyperparameters: (1) lambda, the magnitude of the
shrinkage penalty to the coefficients, and (2) alpha, the degree of mixing between ridge regression
and lasso. The elastic net GLM provides an interpretable equation to describe the relationship
between outcome and predictor(s) that is often familiar even to non-statisticians. The algorithm
here handles missing continuous data by mean imputation, and variable importance is ranked by
the highest magnitude (absolute value) of the regression coefficients.
Random Forest (RF). The random forest was originally developed by Breiman (2001) by
creating an ensemble of decision trees across bootstrapped resamples of data with random selection
among a subset of predictors. A single decision tree is a simple data mining algorithm in its own
right that iteratively partitions a data set by splitting on the variable that may best discriminate an
outcome. At each stage, the decision tree selects the best possible variable for splitting without
regard to how future splits may be influenced. This constitutes a “greedy” approach that is
susceptible to high variance.
The random forest improves on the decision tree in two notable ways: (1) variance is
reduced by averaging across many trees and (2) splitting at any given tree node only uses a random
subset of predictors, effectively decorrelating the trees in the forest. The algorithm may also
internally handle missing data by allowing splits for missing values. Random forests are governed
by three primary hyperparameters (although others may be included): the number of trees in the
forest, the depth of each tree (the total number of splits a given tree may make), and mtry, the
number of randomly-chosen variables to consider at each split. Random forest variable importance
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
is calculated by randomly permuting the values of each predictor; to the extent that the
performance of the algorithm changes, the variable may be considered important.
Gradient Boosting Machine (GBM). Similar to the random forest, the GBM (Friedman,
2001, 2002) builds a strong prediction model from an ensemble of weaker models (here, decision
trees, although other types of models may be used). However, rather than building a collection of
trees on resampled data sets, boosted models are built sequentially by (1) fitting an initial model
(a decision tree), then (2) fitting a new decision tree to the residuals of the initial model and adding
it to the fitted first model (with a shrinkage penalty) to update the residuals. This process is repeated
over several iterations, constantly updating residuals, to find ways to fit the hardest-to-learn
observations. This algorithm as implemented in H2O (Click, Malohlava, Candel, Roark, & Parmar,
2016) handles missing data similarly to the random forest, and is governed by several
hyperparameters including the shrinkage rate lambda (on average, slower learning algorithms
perform better, but may be more computationally expensive), the number of trees to fit, and the
depth of the trees. Variable importance is also provided by the algorithm in terms of absolute and
relative prediction strength of each input variable.
Deep Learning (DL). Deep learning, implemented in H2O as a novel version of the neural
network (Candel, Parmar, LeDell, & Arora, 2016) builds a model of weighted nonlinear
relationships between nodes called neurons (mimicking the brain structure) by conceiving one or
more hidden layers between a set of inputs and an outcome. The weights of each linked neuron
adapt to minimize error in training data. Deep learning algorithms are particularly useful for speech
and image recognition tasks. Hyperparameters include values for regularization, the number of
hidden layers, the number of nodes within each hidden layer, and others. Missingness on
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
continuous variables is handled via mean imputation, and variable importance is calculated by
examining the weights of the first two layers of the network.
Data Mining Model Evaluation
After tuning each algorithm using a random grid search to optimize hyperparameter values,
variable importance metrics were collected, and the best algorithm of each type was evaluated on
the test set. This evaluation yields a predicted probability for each classification for each algorithm;
for example, when comparing hybrid versus pure financial elder abuse, each of the best-tuned
generalized linear models, random forests, gradient boosting machines, and deep learning models
provided a probability between 0 and 1 of a test set observation being a “pure” or a “hybrid” case
of financial elder abuse.
These predicted probabilities require further investigation. The naïve investigative
principal would be to determine classification of outcomes based on a predicted probability of 0.5
or greater; that is, if an observation is at least 50% likely to be a given classification (e.g., pure),
then that observation would be labelled thusly. However, this threshold does not always optimize
classification in a practical sense. First, it does not optimize accuracy itself: one may have a larger
percentage of correct classification into either group using a different threshold. Second, correct
classifications and incorrect classifications may not be equally important. One commonly-used
threshold is the F
1
value: the harmonic mean between sensitivity (true positive rate) and precision
(ratio of observations correctly classified to the number of observations predicted for a given
category). By default, H2O will provide the optimized threshold to maximize F
1
and report a
contingency table based thereon. However, given that correct and incorrect predictions may have
different costs, researchers should still examine and discern the cutoff that best optimizes the costs
inherent to a given research problem.In addition to finding an optimal metric for classifying
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
observations into categories, the area under the receiver operating characteristic curve (AUROC,
or more commonly AUC) provides a general idea of model discrimination performance. The ROC
curve plots true positives against false positives and the closer to 1.0, the better.
A final note about model evaluation bears note: the model with the best predictive
power/best discrimination of the outcome may also be the most difficult to interpret. The GLM is
the most readily interpretable algorithm in every case: parameter coefficients describe the
magnitude and direction of influence for each variable in the model. The random forest, gradient
boosting machine, and deep learning algorithms provide variable importance metrics, but as noted
these are generally “black boxes” and determining the direction of influence is nebulous. Stacked
ensembles are even more difficult to interpret: these provide raw predictive power, and the only
interpretable output is the individual contribution of the constituent algorithms from the tuning
process (e.g., each algorithm has a different weight).
Modeling Decisions
The approach taken for this analysis was to each individual’s first case of substantiation to
define their type of abuse. This decision was made for two reasons. First individuals could be in
the system multiple times and thus, using the first date of substantiation reduced the need for
randomly selecting which case to use. Second, because these data derive from APS cases,
recidivistic cases may confer more information than first time cases and thus, might need to be
weighted differently because an investigator may know more about the case due to prior known
information and thus, may validate the case based on this information. This could affect the ability
to identify important risk factors and characteristics associated with the outcome. We also modeled
the data using a variety of approaches within the supervised learning program. This allows us to
identify the most robust and accurate model given the data.
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Results
Because recidivism may play a unique role in the level of known information about a case
(i.e. assessor may have more information on previously investigated cases than on initial
investigations) and thus adding an unequal prediction weight, we chose to truncate the analysis to
include only the first episode of confirmed abuse. The total count for the confirmed elder abuse
cases between the years 2009 and 2014 was N = 8,800. A total of N = 2514 or (29%) of the
confirmed elder abuse cases over the 5-years include FE. A total of N=1964 (78%) had
substantiated FE only (i.e. Pure FE) and N = 550 had FE plus some other form(s) of abuse (i.e.
Hybrid FE), excluding self-neglect. Tables 1-4 describe the victim and perpetrator demographics
as well as cognitive, functional and substance abuse characteristics that are collected as part of the
routine APS investigation in addition to the CARE tool variables.
For brevity, only the main results pertaining to the specific aims are provided in the
narrative. Two sets of results are presented to balance interpretation and predictive accuracy of the
models used to address the specific aims. These models include the General Linear Model (GLM)
for interpretation and the Gradient Boosting Machine (GBM) for predictive and classification
accuracy. Tables 5-10 provide the details regarding the GLM and GBM findings when trying to
differentiate between confirmed FE and other forms of confirmed abuse and confirmed pure FE
versus confirmed Hybrid FE. Receiver operating curves for all algorithms presented below can be
found in Figures 1-4 located in the Appendix.
Beginning with the most interpretative model, 4 of the top 10 most important variables for
differentiating confirmed FE versus other forms of confirmed abuse included financial based
questions (Table 5). Interestingly, the second most important variable in the model was apparent
injuries which predicted other forms of abuse. Three of the last 5 most important variables are
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
related to caregiver neglect issues such as stress and burnout, knowledge and ability and physical
neglect of the older adult. Differentiating characteristics of the perpetrator include being a spouse
and older than 65 years of age; both of which are protective against FE. While area under the curve
(AUC) for classifying confirmed FE versus other confirmed abuse cases was good (0.97), this
model had the highest mean square error (MSE) rate (0.059) indicating less classification
reliability compared to the other models (Table 6).
[Insert Table 5 & 6]
These AUC (0.799) and the MSE (0.125) worsen when trying to differentiate confirmed
pure FE from confirmed hybrid FE (Table 8). Likewise, the variables of importance changed with
no financial based questions making the top 10 list and the addition of other variables including
inadequate medical supplies, foreclosure and evictions, restricted autonomy, inadequate food
supply and alcohol and drug use by others in the home (Table 7).
[Insert Table 7 & 8]
The GBM sacrifices interpretative detail to maximize predictive accuracy. Table 9 provides
the top 10 variables of importance for differentiating confirmed FE from other confirmed types of
abuse. This model, like the GLM model found 3 financial questions to be within the top 4 most
important variables for classification. Unauthorized use of the victim’s income/assets by others
was the most important variable from which other variables were scaled in relation to this variable.
While other variables are included in the top 10, their scaled importance is quite limited dropping
to less than 10% contribution to the group prediction beginning with perpetrator relationship
identified as other. The model AUC and MSE were 0.972 and 0.053, respectively (Table 6).
[Insert Table 9]
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Differentiating confirmed pure FE versus confirmed Hybrid FE provided a set of top 10
variables which individually contributed more in comparison to the model found in Table 10. Table
10 identified a different set of variables with APS region where the allegation was substantiated
being the top variable of importance for differentiating the group. In this model, it is also
determined that the variables related to negative effects of others, alcohol and drug use by others
in the home, facing foreclosure and inadequate medical supplies were ranked the highest in
importance for predicting pure FE. Interestingly, the only financial-based question included in the
top 10 was evidence of substantial unusual activity with the client’s financials or assets by other(s).
The AUC and MSE for this model 0.831 and 0.123, respectively (Table 8).
[Insert Table 10]
Discussion
This study utilized a large statewide dataset of confirmed elder abuse cases to form data-
driven risk factor models that differentiate elder FE from other types of abuse and pure FE from
hybrid FE. These models were developed using machine learning algorithms capable of handling
very large aggregated datasets in which it is suspected that victim level, perpetrator level and
community-level data interact in myriad unspecified ways to increase or decrease the risk of the
outcome. Seeking to balance interpretative model building with predictive accuracy model
building we found parallels with earlier research (Jackson & Hafemesiter, 2012), but also
identified new factors, across multiple levels of the socioecological context, to be considered when
trying to differentiate other forms of abuse from FE and when trying to differentiate pure vs hybrid
FE.
To create the context in which our findings should be considered, we first present a few
study limitations. Although this was a large dataset of confirmed elder abuse cases over a five-
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
year timeframe, the data represented case findings from a single APS organization. It is understood
that APS agencies across the country may have different statutes, definitions and investigation
techniques thus, reducing the generalizability of the findings and the use of the data algorithms
available for predicting the outcomes. Also, the APS organization from which these data were
derived only investigates FE that occurs within a trusted relationship between the victim and
perpetrator. Thus, financial scams and most cases of fraud were not included. Moreover, only elder
abuse cases were included in the analysis, therefore excluding self-neglect which could also be
important for understanding the risks of being financially exploited (Dong et al., 2013). Crime data
at the community-level were not included due to little comparable and available data across the
counties. This information could be highly useful for identifying locations where public service
announcements may have the highest impact for prevention and intervention. Finally, due to
truncating the data analysis to the first confirmed case of abuse, recidivism was not included as a
risk factor despite its potential importance in differentiating types of abuse (Jackson and
Hafemeister, 2012).
Differentiating FE from other forms of abuse resulted in a few variables of importance that
were not altogether unsuspected. It was no surprise that three of the top four most important
variables in both the GLM and GBM models were financially focused given that evidence of these
would indicate some sort of financial exploitation attempt. Nor was it of great surprise that
caregiver stress and burnout, knowledge and willingness to care for the client were more predictive
of other forms of abuse since these conditions have been linked both theoretically and empirically
to poor provision of medical and physical care (Reis & Namiash, 2008). It was also found in this
model that spousal perpetrators and those 65 years of age and older were more likely to be
associated with other forms of abuse. This finding fits with previous research and suggests that
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
when FE is involved perpetrators outside of these characteristics (i.e. adult children, grandchildren,
neighbors) should be considered as more probable (Jackson & Hafemeister, 2012; Hafemeister,
2003).
Interestingly, apparent injury to the client was the second most important variable in the
GLM model, outperforming caregiver’s management of victim’s finances and evidence of
substantial unusual activity with the victim’s financials by others. In the pure FE versus hybrid
FE model, apparent injuries became the variable with the greatest importance for predicting FE
status. This indicates that apparent injury is a salient indicator that should be looked for even when
FE is the only reported allegation. The presence of an apparent injury during an FE investigation
may very well be an indicator of some concurrent form of abuse (i.e. Hybrid FE). Alternatively,
when an apparent injury is present it may also indicate the need to concurrently rule out FE as a
motive for the injury. Jackson and Hafemeister (2012) found that Hybrid FE victims experienced
various forms of abuse which could have manifested as apparent injuries. Another interesting
variable that predicted other forms of abuse was thoughts of suicide and self-injury. While previous
studies have linked FE to outcomes such as depression and suicide (Nerenberg, 2000; Podnieks,
1992), it appears that in these data, FE victimization was not as strongly associated with these
feelings compared to being victimized in other ways. It could also be that the earlier study did not
account for the presence of other forms of abuse when assessing the association between FE and
depression and suicide therefore, making these distinctions is of underlying importance.
The GLM model differentiating pure FE from hybrid FE should be given more specific
consideration. Previous research has found that FE victimization is the least likely form of abuse
in older adults to be prosecuted and to receive follow-up from APS caseworkers and other agencies
(Jackson and Hafemeister, 2011). A plausible reason for this finding is the lack of attention paid
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
to the need for differentiating the types of abuse and making the association with outcomes that
impact quality of life. Review of the GLM model, shows that when FE is associated with other
forms of abuse a range of quality of life issues are negatively impacted. The older adult may not
be receiving their adequate medical supplies due to a lack of funds. They may be facing
foreclosure, living with no utilities and inadequate food supplies and in conditions that may be
condemnable. Moreover, they may be deprived of one of the most essential conditions of being an
adult which is autonomy to make one’s own decisions and have one’s own purpose. This could
account for the previous finding that these older adults are having more thoughts of suicide and
self-injury. It is highly plausible that these conditions are the result of longer-term abuse (Jackson
and Hafemeister, 2012) and thus, speak to the need for identifying FE and differentiating pure FE
from hybrid FE when a case is first investigated.
The GBM model for both differentiating FE from other forms of abuse and pure FE from
hybrid FE provided the best classification accuracy. As mentioned above, financially-based
questions were of the greatest importance in the differentiating the former. However, it was found
that APS region was the fifth most important predictor of FE in this model, but was the first most
important in the model predicting pure versus hybrid FE. This may point to regions where public
service announcements about financial crimes may benefit older adults living in the areas or point
to other community-level variables that were not included such as crime data which are often hard
to standardize and obtain in a way that allows comparison across counties. Other highly important
variables that predicted pure FE was negative effects of others on the older adult as well as alcohol
and drug use by others in the house. While GBM models are less interpretive it is plausible that
when victims are more affected by others in the home and when alcohol and drug use by others
are present, then pure FE is less likely. Negative effects may be related to any of the other forms
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
of abuse including psychological abuse and alcohol and drug abuse by others in the home was
predictive of hybrid FE in the earlier GLM model which also fits with literature about perpetrator
characteristics. Other variables such as having an ongoing relationship conflict with others and the
perpetrator being more likely to be a child also suggest that these variables are predictive of hybrid
FE.
This study expanded on the earlier study by Jackson and Hafemeister (2012) which
identified victim and perpetrator factors associated with pure FE versus hybrid FE. While different
sets of variables were considered based on the available data and the definitions of FE, there was
overlap between variables and several of the findings were comparable. These studies provide
complementary data for understanding FE and its subtypes. Both studies identified troubling
patterns of abuse with the current study point out the importance of apparent injury in
differentiating pure versus hybrid FE. Both studies also identified a lack of appropriate medical
supervision and inadequate food supplies associated with hybrid FE. While Jackson and
Hafemeister reported that a change in living status and longer-term abuse was associated with
hybrid FE the current study found that the hybrid FE victims were more likely to be facing was
facing foreclosure and eviction which plausibly points to both a future change in living status and
longer-term abuse. Moreover, neither study found perpetrator mental health or criminal history to
be important predictors, but the current study did find that alcohol and drug use by others in the
home was more predictive of hybrid FE.
The current study also expanded on previous research by identifying factors of importance
that could help frontline workers differentiate FE from other forms of abuse. Similarly with pure
FE versus hybrid FE, these factors emerge across multiple levels of the socioecological context
suggesting the need for comprehensive assessments when trying to determine whether FE has
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
occurred. Because FE and other forms often occur in highly complex conditions where the change
in a single factor, among many, could affect the probability of an outcome such as pure FE versus
hybrid FE it is important to be able to identify reliable predictors of the outcome to decrease the
likelihood of misclassifying a case which could be detrimental especially if a hybrid FE case is
falsely classified as a pure FE case.
To this end, this study utilized a new and unparalleled approach in the field of elder abuse
and was able to analyze the many different possible interactions within a large and robust APS
dataset to derive the most important variables across the different socioecological levels for
predicting FE from other forms of abuse and pure FE from hybrid FE. Such modeling can be used
to create replicable data algorithms that can be transformed into web-based applications for
immediate broad-based dissemination and use for public health surveillance and program
development by social service and criminal justice agencies as well as researchers.
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
References
Acierno R, Hernandez MA, Amstadter AB, et al. Prevalence and correlates of emotional, physical,
sexual, and financial abuse and potential neglect in the united states: The national elder
mistreatment study. Am J Public Health. 2010;100(2):292-297.
Amstadter A. B., Zajac K., Strachan M., Hernandez M. A., Kilpatrick D. G., Acierno R. (2011).
Prevalence and correlates of elder mistreatment in South Carolina: The South Carolina elder
mistreatment study. Journal of Interpersonal Violence, 26, 2947-2972.
Anetzberger GJ, Korbin JE & Austin C. Alcoholism and Elder Abuse. J Interpers. Violence, 1994,
9(2):184-193.
Breiman, L. (2001). Random forests. Machine Learning, 45(1), 5-32.
Burnett J, Dyer CB, Green CE, Flores DV, Booker JG & Diamond PM. Community-Based Risk
Assessment of Elder Mistreatment and Self-Neglect: Evidence of Construct Validity and
Measurement Invariance Across Gender and Ethnicity. The Journal of the Society for Social Work
and Research, 2014.
Burnett J, Jackson SL, Sinha A, Aschenbrenner AR, Xia R, Murphy KP & Diamond PM.
Differential Mortality across Five Types of Substantiated Elder Abuse. Journal of Elder Abuse and
Neglect, 2016; 28:2, 59-75.
Candel, A., Parmar, V., LeDell, E., & Arora, A. (2016). Deep learning with H2O (5
th
ed.).
Mountain View, CA: H2O.ai, Inc.
Choi, NG, Kulick DB., & Mayer, J. (1999). Financial exploitation of elders: Analysis of risk
factors based on county adult protective services data. Journal of Elder Abuse and Neglect, 10, 39-
62.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Click, C., Malohlava, M., Candel, A., Roark, H., & Parmar, V. (2016). Gradient boosted models
with H2O (6
th
ed.). Mountain View, CA: H2O.ai, Inc.
Coker J, & Little B. (1997). Investing in the future: Protecting the elderly from financial abuse.
FBI Law Enforcement Bulletin, 1-5.
Department of Human Services and Department of Protective and Regulatory Services.
Investigations and Protective Services for Elderly and Disabled Persons, Human Resources Code,
Chapter 48. Subchapter A. General Provisions. 2009;
http://www.statutes.legis.state.tx.us/Docs/HR/htm/HR.48.htm. Accessed February 27, 2017
Dessin, CL. (2000). Financial abuse of the elderly. Idaho Law Review, 36, 203-226.
Dong X, Simon MA. Association between elder abuse and use of ED: findings from the Chicago
Health and Aging Project. American Journal of Emergency Medicine 2013;31:693-698.
Dong X & Simon MA. Elder abuse as a risk factor for hospitalization in older persons. JAMA
Intern Med. 2013, 173(10):911-917.
Dong X, Simon M, Evans D. Elder self-neglect is associated with increased risk for elder abuse in
a community-dwelling population: Findings from the Chicago health and aging project. J Aging
Health. 2013;25(1):80-96.
Ernst JS. (2000). Community-level factors and child maltreatment in a suburban county. Soc Work
Res. 2001. 25(3):133-142.
Friedman, J.H. (2001). Greedy function approximation: A gradient boosting machine. Annals of
Statistics, 29(5), 1189-1232.
Friedman, J. H. (2002). Stochastic gradient boosting. Computational Statistics and Data Analysis,
38(4), 367-378.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Hafemeister, TL. Elder Mistreatment: Abuse, Neglect and Exploitation in an Aging America. In
the National Research Council (US) Panel to Review Risk and Prevalence of Elder Abuse and
Neglect. J. Bonnie & R. Wallace (eds.) National Academies Press (US). Washington DC. 2003
Hastie, T., Tibshirani, R., & Friedman, J. H. (2009). The elements of statistical learning: Data
mining, inference, and prediction (2
nd
ed.). New York, NY: Springer.
Hirshorn, B., & Stewart, J. (2003). Geographic information systems in community-based
gerontological research and practice, Journal of Applied Gerontology, 22(1), 134-151.
Jackson, S. L., & Hafemeister, T. L. (2011). Risk factors associated with elder abuse: The
importance of differentiating by type of elder maltreatment. Violence and Victims, 26(6), 738-757.
Jackson SL &TL Hafemeister. Pure financial exploitation versus hybrid financial exploitation co-
occurring with physical and/or neglect of elderly persons. Psychol of Violence, 2012; 2(3):285-
296.
Kemp BJ & Mosqueda LA. Elder financial abuse: an evaluation framework and supporting
evidence. J Am Geriatr. Soc., 2005, Jul. 53(7):1123-7.
Kuhn, M. & Johnson, K. (2013). Applied predictive modeling. New York, NY: Springer.
Aiello, S., Kraljevic, T., & Maj, P. (2016). h2o: R Interface for H2O. R package version 3.8.3.3.
http://www.h2o.ai/.
Laumann E. O., Leitsch S. A., Waite L. J. (2008). Elder mistreatment in the United States:
Prevalence estimates from a nationally representative study. Journal of Gerontology, 63, 48-54.
LeDell, E. (2016). h2oEnsemble: H2O ensemble learning. R package version 0.1.8.
https://github.com/h2oai/h2o-3/tree/master/h2o-r/ensemble/h2oEnsemble-package.
Metlife (Metlife Mature Market Institute, National Committee for the Prevention of
Elder Abuse, & the Center for Gerontology at Virginia Polytechnic Institute and

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
State University) (2009). Broken trust: Elders, family, and finances. Retrieved
from: http://www.metlife.com/assets/cao/mmi/publications/studies/mmistudy-
broken-trust-elders-family-finances.pdf
National Center on Elder Abuse. What is elder abuse? https://ncea.acl.gov/faq/index.html#faq1
Nerenberg L. (2000). Forgotten victims of financial crime and abuse: Facing the challenge. Journal
of Elder Abuse and Neglect, 12, 49-72.
Nykodym, T., Kraljevic, T., Hussami, N., Rao, A., & Wang, A. (2016). Generalized linear
modeling with H2O (5
th
ed.). Mountain View, CA: H2O.ai, Inc.
Peterson JC, Burnes DPR, Caccamise PL, Mason A, Henderson Jr. CR, Wells MT, Berman J,
Cook AM, Shukoff D, Brownell P, Powell M, Salamone A, Pillemer KA & Lachs M. Financial
exploitation of older adults: A problem-based prevalence study. J Gen Intern Med. 2014, Dec.
29(12):1615-1623.
Payne BK & Gainey RR. Mapping elder mistreatment cases: interactions between mistreatment,
dementia, service utilization, access to services and disadvantage. Journal of Human Behavior and
Social Environment, 2009; 19(8):1025-1041.
Pillemer K. (2005). Elder abuse is caused by deviance and dependence of abusive caregivers. In
D.R. Loseke, R.J. Gelles, & M.M. Cavanaugh (Eds.), Current controversies on family violence
(2
nd
ed. Pp. 207-220). Thousand Oaks, CA: Sage.
Podnieks E. National survey on abuse of the elderly in Canada. Journal of Elder Abuse and
Neglect, 1992, 4, 5-58.
R Core Team (2016). R: A language environment for statistical computing. R Foundation for
Statistical Computing, Vienna, Austria. URL http://www.R-project.org/.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Reis M, Nahmiash D. Validation of the indicators of abuse (IOA) screen. Gerontologist.
1998;38:471–480.
Steinberg SJ, & Steinberg SL. GIS: Geographic Information Systems for Social Sciences:
Investigating Space and Place. 1
st
Edition. 2006. SAGE Publications, Thousand Oaks, CA 91320.
Teaster PB, Otto JM, Dugar TA, Mendiondo MS, Abner EL, Cecil KA. The 2004 survey of state
adult protective services: Abuse of adults 60 yrs and older.
http://www.ncea.aoa.gov/NCEAroot/Main_Site/pdf/2-14-06%20FINAL%2060+REPORT.pdf.
Updated 2010. Accessed April/4, 2011.
Tabachnick BG, Fidell LS. Using Multivariate Statistics. 4th ed. Needham Heights, MA: Pearson
Education Company; 2001.
Witten, I. H., Frank, E., & Hall, M. A. (2011). Data mining: Practical machine learning tools and
techniques (3
rd
ed.). Burlington, MA: Morgan Kaufmann.
Witten, JD, Hastie, T., & Tibshirani, R. (2013). An introduction to statistical learning: With
applications in R. New York, NY: Springer.
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
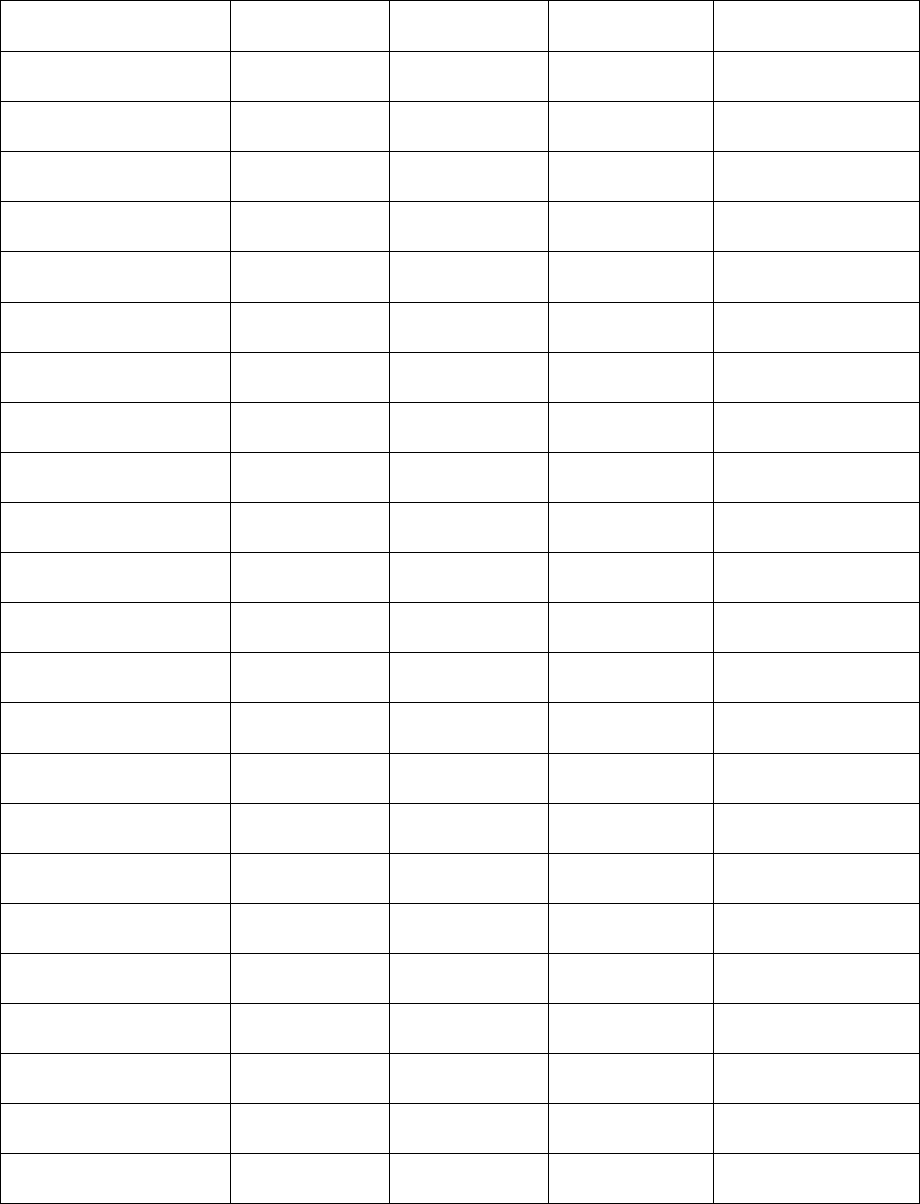
Table 1: Victim Demographic Characteristics for N = 113561 Adult Protective Services Substantiated
Cases of Elder Abuse in Texas Between the Years of 2009 - 2014
All Confirmed
FE
Confirmed
Pure FE
Confirmed
Hybrid FE
Confirmed Other
Abuse-No FE
N=2514
N=1964
N=550
N=6286
Age
65-69
331(13.2)
238(12.1)
93(16.9)
1456(23.2)
70-74
397(15.8)
282(14.4)
115(20.9)
1334(21.2)
75-79
462(18.4)
358(18.2)
104(18.9)
1224(19.5)
80-84
565(22.5)
454(23.1)
111(20.2)
1176(18.7)
85-89
475(18.9)
390(19.9)
85(15.5)
731(11.6)
90+
284(11.1)
242(12.3)
42(7.6)
365( 5.8)
Gender
Female
1692(67.3)
1311(66.8)
381(69.3)
4365(69.4)
Male
814(32.4)
648(33.0)
166(30.2)
1908(30.4)
Missing
8(0.30)
5( 0.3)
3( 0.5)
13(0.2)
Ethnicity
White
1561(62.1)
1221(62.2)
340(61.8)
3519(56.0)
Black
331(13.2)
247(12.6)
84(15.3)
789(12.6)
Hispanic
423(16.8)
312(15.9)
111(20.2)
1735(27.6)
Other
199(7.9)
184(9.4)
15( 2.7)
226( 3.6)
Marital
Married
499(19.8)
380(19.3)
119(21.6)
2532(40.3)
Divorced
159(6.3)
109( 5.5)
50( 9.1)
405(6.4)
Widowed
851(33.9)
648(33.0)
203(36.9)
1436(22.8)
Separated
16(0.7)
13( 0.7)
3( 0.5)
58( 0.9)
Single
66(2.6)
43( 2.2)
23( 4.2)
154( 2.4)
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Missing
923(36.7)
771(39.3)
152(27.6)
1701(27.1)
Living
Own home/apt
1706(67.9)
1337(68.1)
369(67.1)
5048(80.3)
Friends/relatives
233(9.3)
173( 8.8)
60(10.9)
718(11.4)
Nursing home/assisted
living
513(20.4)
404(20.6)
109(19.8)
357( 5.7)
Other
61(2.4)
49( 2.5)
12( 2.2)
152( 2.4)
Missing
1(0.1)
1( 0.1)
0( 0.0)
11( 0.2)
FE = Financial Exploitation; Pure FE = Financial Exploitation Only Excluding Hybrid Cases; Hybrid
FE = Financial Exploitation Plus Other Types of Abuse Excluding Pure FE; Other Abuse = Caregiver
Neglect, Psychological Abuse, Physical Abuse;
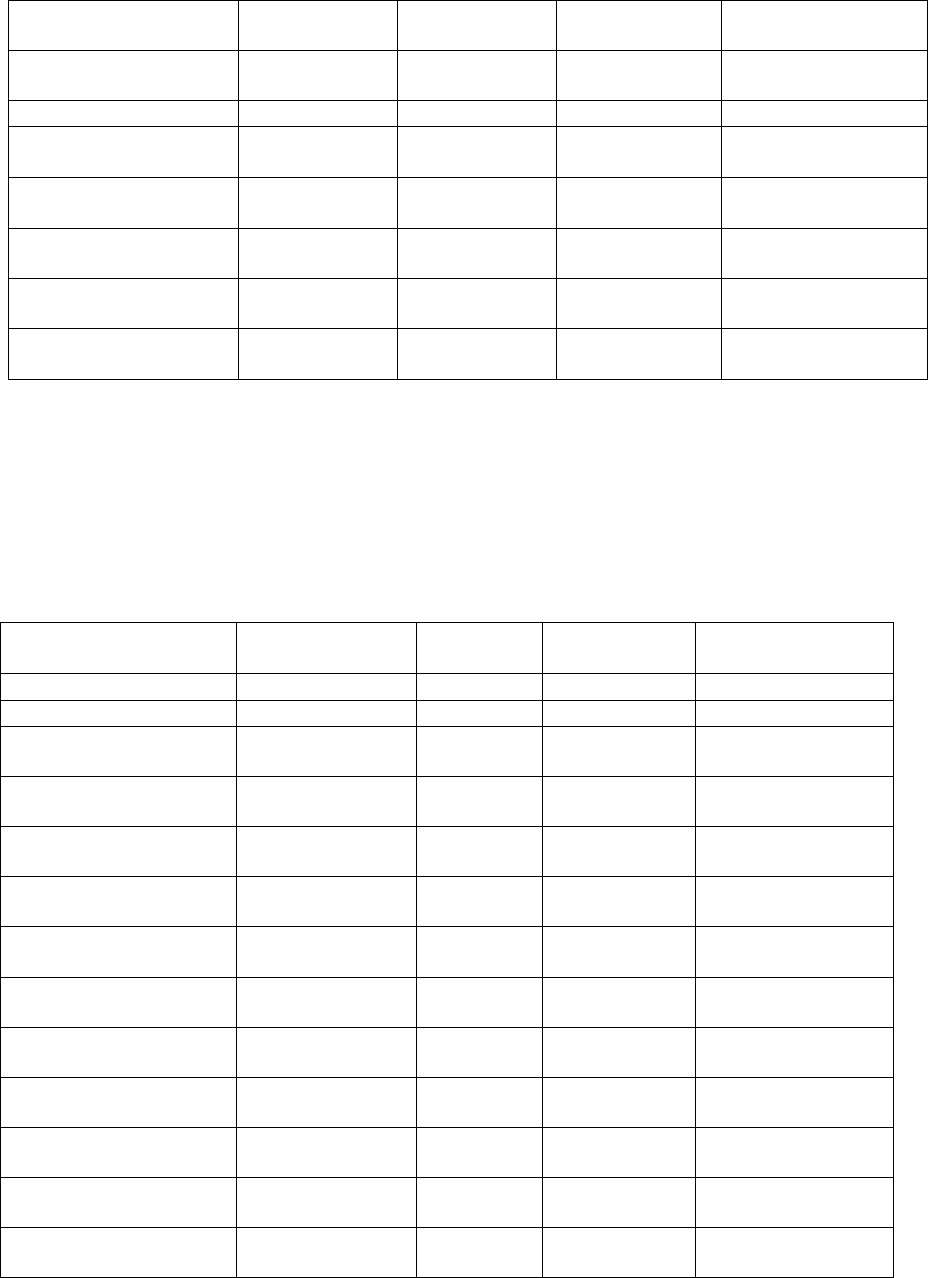
Table 2: Victim Impairment and Substance Abuse Characteristics for N = 113561 Adult Protective
Services Substantiated Cases of Elder Abuse in Texas Between the Years of 2009 - 2014
All Confirmed
FE
Confirmed
Pure FE
Confirmed
Hybrid FE
Confirmed Other
Abuse-No FE
N=2514
N=1964
N=550
N=6286
Cognitive Impairment
N
2178(86.6)
1713(87.2)
465(84.5)
5847(93.0)
Y
336(13.4)
251(12.8)
85(15.5)
439(7.0)
Alcohol abuse
N
2500(99.4)
1950(99.3)
550(100.0)
6237(99.2)
Y
14(0.6)
14( 0.7)
0( 0.0)
49( 0.8)
Drug abuse
N
2512(99.9)
1962(99.9)
550(100.0)
6273(99.8)
Y
2(0.1)
2( 0.1)
0( 0.0)
13( 0.2)
Physically disabled
N
1868(74.3)
1472(74.9)
396(72.0)
4993(79.4)
Y
646(25.7)
492(25.1)
154(28.0)
1293(20.6)
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Mobility impairment
N
1954(77.7)
1529(77.9)
425(77.3)
5370(85.4)
Y
560(22.3)
435(22.1)
125(22.7)
916(14.6)
Visual Impairment
N
2423(96.4)
1894(96.4)
529(96.2)
6108(97.2)
Y
91(3.6)
70( 3.6)
21( 3.8)
178( 2.8)
Hearing impairment
N
2396(95.3)
1879(95.7)
517(94.0)
6102(97.1)
Y
118(4.7)
85(4.3)
33(6.0)
184( 2.9)
Limited English
N
2392(95.1)
1870(95.2)
522(94.9)
5702(90.7)
Y
122(4.9)
94( 4.8)
28( 5.1)
584( 9.3)
Developmental
Disability
N
2510(99.8)
1961(99.8)
549(99.8)
6273(99.8)
Y
4(0.2)
3( 0.2)
1( 0.2)
13( 0.2)
FE = Financial Exploitation; Pure FE = Financial Exploitation Only Excluding Hybrid Cases; Hybrid
FE = Financial Exploitation Plus Other Types of Abuse Excluding Pure FE; Other Abuse = Caregiver
Neglect, Psychological Abuse, Physical Abuse;

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
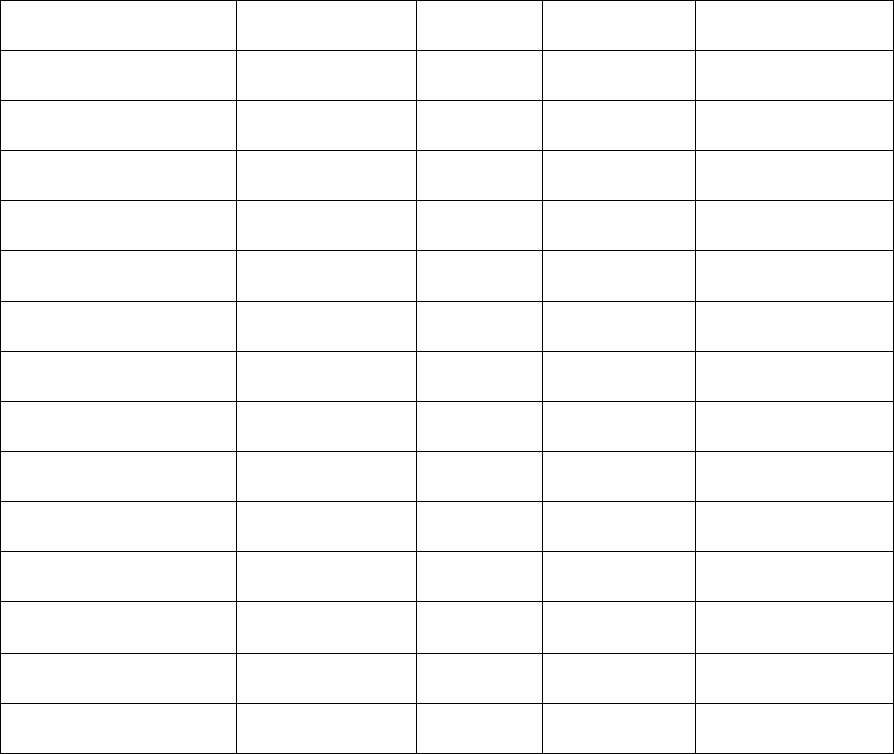
Table 3: Characteristics for N = 15705 Texas Adult Protective Services Substantiated Perpetrators of
Elder Abuse in Between the Years of 2009 - 2014
All Confirmed
FE
Confirmed
Pure FE
Confirmed
Hybrid FE
Confirmed Other
Abuse-No FE
N=4203
N=3099
N=1104
N=11502
Age
0-24
404(10)
317(10.2)
87( 7.9)
1327(11.5)
25-29
321(8)
264( 8.5)
57( 5.2)
473( 4.1)
30-34
390(9)
298( 9.6)
92( 8.3)
539( 4.7)
35-39
449(11)
336(10.8)
113(10.2)
722( 6.3)
40-44
566(13)
409(13.2)
157(14.2)
1042( 9.1)
45-49
670(16)
466(15.0)
204(18.5)
1352(11.8)
50-54
589(14)
407(13.1)
182(16.5)
1435(12.5)
55-59
421(10)
300( 9.7)
121(11.0)
1044( 9.1)
60+
393(9)
302( 9.7)
91( 8.2)
3568(31.0)
Gender
Female
2542(60)
2001(64.6)
541(49.0)
5337(46.4)
Male
1674(39)
1075(34.7)
559(50.6)
6127(53.3)
Missing
27(1)
23( 0.7)
4( 0.4)
38( 0.3)
Ethnicity
White
2070(49)
1448(46.7)
622(56.3)
5934(51.6)
Black
792(19)
604(19.5)
188(17.0)
1591(13.8)
Hispanic
899(21)
665(21.5)
234(21.2)
3287(28.6)
Other
442(11)
382(12.3)
60( 5.4)
690( 6.0)
Missing
0(0)
0( 0.0)
0( 0.0)
0( 0.0)
Marital
Married
880(21)
658(21.2)
222(20.1)
3592(31.2)
Divorced
323(8)
215( 6.9)
108( 9.8)
808( 7.0)
Widowed
53(1)
39( 1.3)
14( 1.3)
184( 1.6)
Separated
77(2)
57( 1.8)
20( 1.8)
234( 2.0)
Single
452(11)
301( 9.7)
151(13.7)
1674(14.6)
Missing
2418(58)
1829(59.0)
589(53.4)
5010(43.6)
Living
Own home/apt
2094(50)
1622(52.3)
472(42.8)
5487(47.7)
Friends/relatives
946(23)
593(19.1)
353(32.0)
3312(28.8)
Nursing
home/assisted
living
4(0.009)
2( 0.1)
2( 0.2)
157( 1.4)
Other
330(8)
226( 7.3)
104( 9.4)
793( 6.9)
Missing
829(20)
656(21.2)
173(15.7)
1753(15.2)
FE = Financial Exploitation; Pure FE = Financial Exploitation Only Excluding Hybrid Cases; Hybrid FE
= Financial Exploitation Plus Other Types of Abuse Excluding Pure FE; Other Abuse = Caregiver Neglect,
Psychological Abuse, Physical Abuse;
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
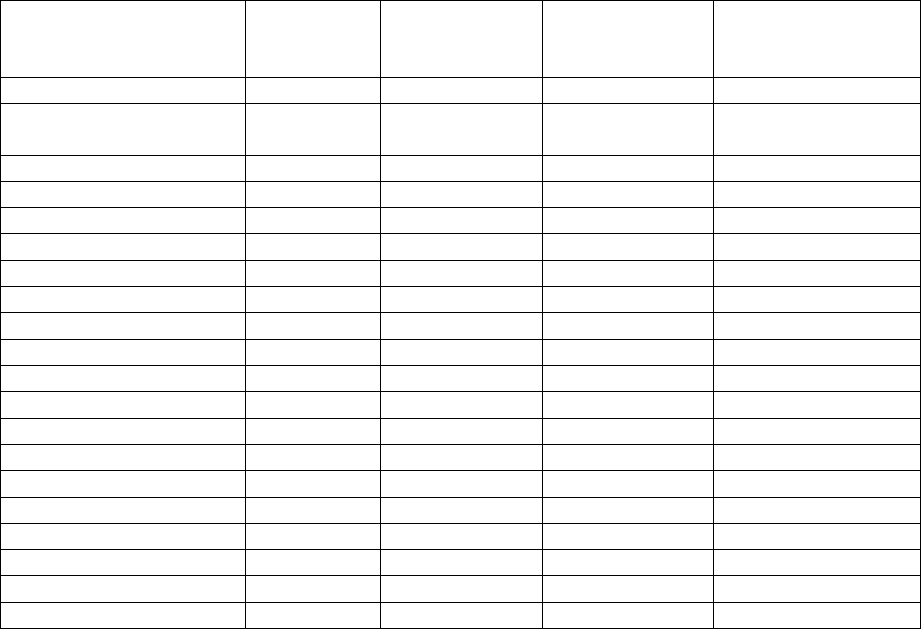
Table 4: Relationship, Co-habitation and Substance Abuse Characteristics for N = 15705 Texas Adult
Protective Services Substantiated Perpetrators of Elder Abuse in Texas Between the Years of 2009 - 2014
All
Confirmed
FE
Confirmed
Pure FE
Confirmed
Hybrid FE
Confirmed Other
Abuse-No FE
N=4203
N=3099
N=1104
N=11502
Relation to
victim
Spouse
81(0.02)
49( 1.6)
32( 2.9)
2720(23.6)
Daughter
884(21)
595(19.2)
289(26.2)
2466(21.4)
Son
896(21)
537(17.3)
359(32.5)
2962(25.8)
Grandchild
606(14)
445(14.4)
161(14.6)
1558(13.5)
Other Family member
518(12)
387(12.5)
131(11.9)
1137( 9.9)
service provider
763(18)
690(22.3)
73( 6.6)
350( 3.0)
Other
394(9)
346(11.2)
48( 4.3)
289( 2.5)
Missing
61(1)
50( 1.6)
11( 1.0)
20( 0.2)
Co-reside with victim
Yes
730(17)
453(14.6)
277(25.1)
5205(45.3)
No
1807(43)
1449(46.8)
358(32.4)
2106(18.3)
Missing
1666(40)
1197(38.6)
469(42.5)
4191(36.4)
Alcohol abuse
N
4066(97)
3019(97.4)
1047(94.8)
10869(94.5)
Y
137(3)
80( 2.6)
57( 5.2)
633( 5.5)
Drug abuse
N
3448(92)
2892(93.3)
956(86.6)
10793(93.8)
Y
355(8)
207( 6.7)
148(13.4)
709( 6.2)
FE = Financial Exploitation; Pure FE = Financial Exploitation Only Excluding Hybrid Cases; Hybrid
FE = Financial Exploitation Plus Other Types of Abuse Excluding Pure FE; Other Abuse = Caregiver
Neglect, Psychological Abuse, Physical Abuse;
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Table 5: Top 10 Variables by Importance for Predicting Financial Exploitation versus Other Forms of
Abuse Using General Linear Model Algorithms
Variable Importance
Interpretation
Predicted Group
1: CARE Item 24
Unauthorized Use of the victims
income/assets by others
Financial Exploitation
2: CARE Item 26
Apparent Injuries to Client
Other Forms of Abuse
3: CARE Item 23
Caregivers Management of
Victims Finances are
Problematic
Financial Exploitation
4: CARE Item 25
Evidence of Substantial Unusual
Activity with the Client’s
Financials or Assets by Other(s)
Financial Exploitation
5: CARE Item 38
Client has Thoughts of Suicide,
Homicide or Self-Injury
Other Forms of Abuse
6: CARE Item 55
Caregiver Stress Burnout
Other Forms of Abuse
7: CARE Item 56
Ability, Knowledge and
Willingness to Care for the
Client
Other Forms of Abuse
8: Perpetrator is the Spouse
The perpetrator is the spouse
Other Forms of Abuse
9: CARE Item 29
Grooming, Hygiene and
Cleanliness
Other Forms of Abuse
10: Number of Perpetrators
Older than 64 years of age
The perpetrator is 65 years of
age or older
Other Forms of Abuse
Table 6: Model Fit for Four Supervised Learning Test-Set Algorithms to Predict Financial Exploitation
Versus Other Forms of Abuse using Victim, Perpetrator and Community-Level data
Mean Squared Error
AUROC
GLM
0.0592
0.9680
RF
0.0574
0.9711
GBM
0.0530
0.9723
RDL
0.0577
0.9681
GLM= General Linear Model; RF = Random Forest; GBM = Gradient Boosting Machine; RDL =
Random Deep Learning
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Table 7: Top 10 Variables by Importance for Predicting Pure Financial Exploitation versus Hybrid
Financial Exploitation Using General Linear Model Algorithms
Top 10 Variables of
Importance
Interpretation
Predicted Group
1: CARE Item 26
Apparent Injuries to Client
Hybrid
2: CARE Item 33
Client has Inadequate Medical
Supplies, Medications
Hybrid
3: CARE Item 02
Client Facing Foreclosure,
Eviction, Condemnation
Hybrid
4: CARE Item 55
Caregiver Stress Burnout
Hybrid
5: CARE Item 17
Utilities not working
Hybrid
6: CARE Item 49
Restricted Autonomy
Hybrid
7: CARE Item 19
Inadequate Food Supply
Hybrid
8: Ethnicity
Native American
Pure
9: CARE Item 54
Alcohol, Drug Use by Others in
the Household
Hybrid
10: CARE Item 03
Conditions attract and Harbor
Pests
Hybrid
Table 8: Model Fit for Four Supervised Learning Test-Set Algorithms to Predict Pure Financial
Exploitation Versus Hybrid Financial Exploitation using Victim, Perpetrator and Community-Level data
Mean Squared Error
AUROC
GLM
0.1251
0.7986
RF
0.1255
0.8288
GBM
0.1230
0.8306
RDL
0.1318
0.7626
GLM= General Linear Model; RF = Random Forest; GBM = Gradient Boosting Machine; RDL =
Random Deep Learning
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Table 9: Top 10 Variables by Importance for Predicting Financial Exploitation versus Other Forms of
Abuse Using on Gradient Boosting Machine Algorithms
Variable
Interpretation
Scaled Importance
1: CARE Item 24
Unauthorized Use of the victims
income/assets by others
1.000
2: CARE Item 25
Unusual Financial Activity
0.249
3: CARE Item 23
Caregivers Management of
Victims Finances are
Problematic
0.104
4: Perpetrator Relationship to
Client
Perpetrator relationship is Other
0.058
5: APS-Region
APS Region where Financial
Victimization Occurred
0.043
6: Client and Perpetrator Co-
habitation
Perpetrator not Cohabitating
with Victim
0.036
7: Fiscal Year
Year of Substantiation
0.031
8: CARE Item 50
Client Ongoing Conflict
Relationships with Others
0.026
9: Client and Perpetrator Co-
habitation
Perpetrator Cohabitating with
the Client
0.017
10: Perpetrator Relationship
to Client
Perpetrator is or is not the
Spouse
0.015
APS = Adult Protective Services; CARE tool = Client Assessment and Risk Evaluation tool
Table 10: Top 10 Variables by Importance for Predicting Pure Financial Exploitation versus Hybrid
Financial Exploitation Using on Gradient Boosting Machine Algorithms
Variable
Interpretation
Scaled Importance
1: APS-Region
APS Region where Financial
Victimization Occurred
1.000
2: CARE Item 51
Negative Effects of Others
Actions on the Client
0.787
3: CARE Item 54
Alcohol, Drug Use by Others in
the Household
0.570
4: CARE Item 02
Client Facing Foreclosure,
Eviction, Condemnation
0.503
5: CARE Item 33
Client has Inadequate Medical
Supplies, Medications
0.458
6: CARE Item 50
Client Ongoing Conflict
Relationships with Others
0.399
7: Perpetrator Relationship to
Client
Perpetrator Relationship with
Victim is Other
0.337
8: Fiscal Year
Year of Substantiation
0.307
9: Perpetrator Relationship to
Client
Perpetrator Relationship to the
Client is Child
0.268
10: CARE Item 25
Evidence of Substantial Unusual
Activity with the Client’s
Financials or Assets of Other(s)
0.266
APS = Adult Protective Services; CARE tool = Client Assessment and Risk Evaluation tool
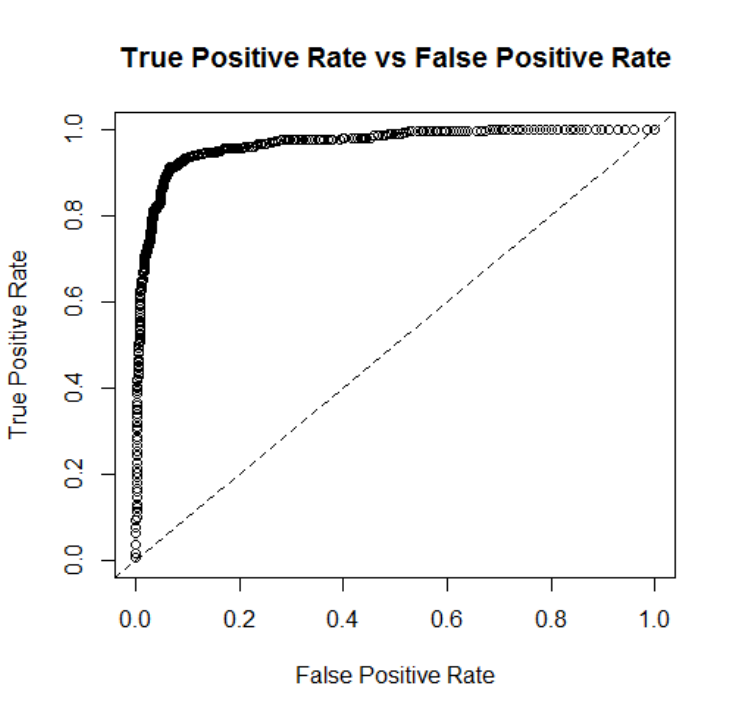
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Figure 1. Area Under the Curve for the General Linear Model When Differentiating Confirmed Financial
Exploitation from Other Confirmed Types of Abuse
Figure 1: The percent correctly classified by chance is 71.46%. This prediction improved to
96.80% using the GLM algorithm.
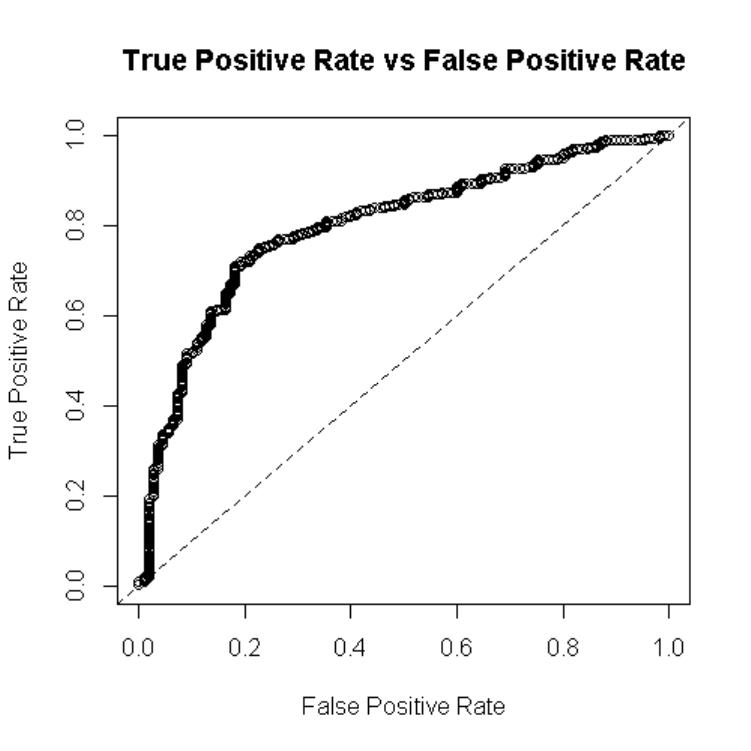
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Figure 2. Area Under the Curve for the General Linear Model When Differentiating Confirmed Pure
Financial Exploitation from Confirmed Hybrid Financial Exploitation
Figure 2: The percent correctly classified by chance is 78.09%. This prediction improved to
79.90% using the GLM algorithm.
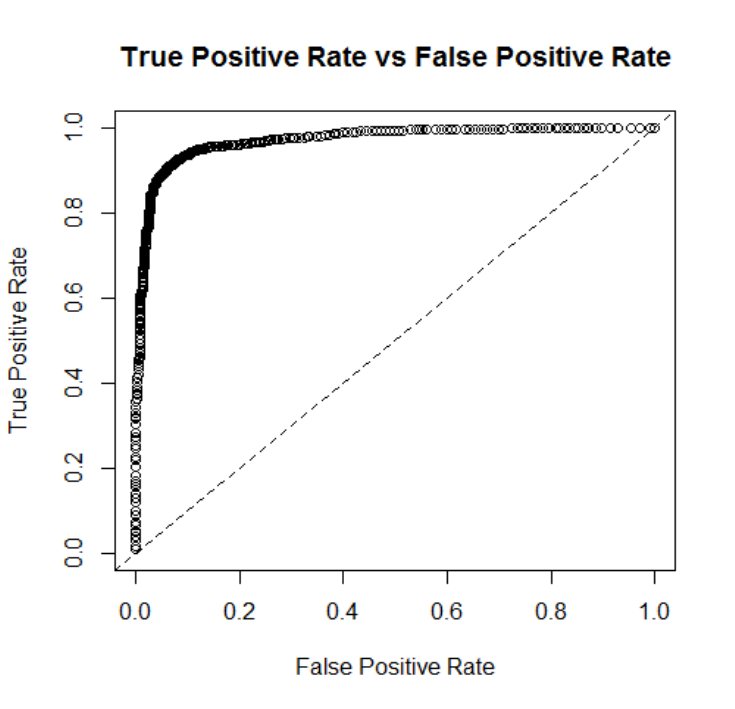
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Figure 3. Area Under the Curve for the Gradient Boosting Machine When Differentiating Confirmed
Financial Exploitation from Other Confirmed Types of Abuse
Figure 3: The percent correctly classified by chance is 71.46%. This prediction improved to
97.23% using the GBM algorithm.
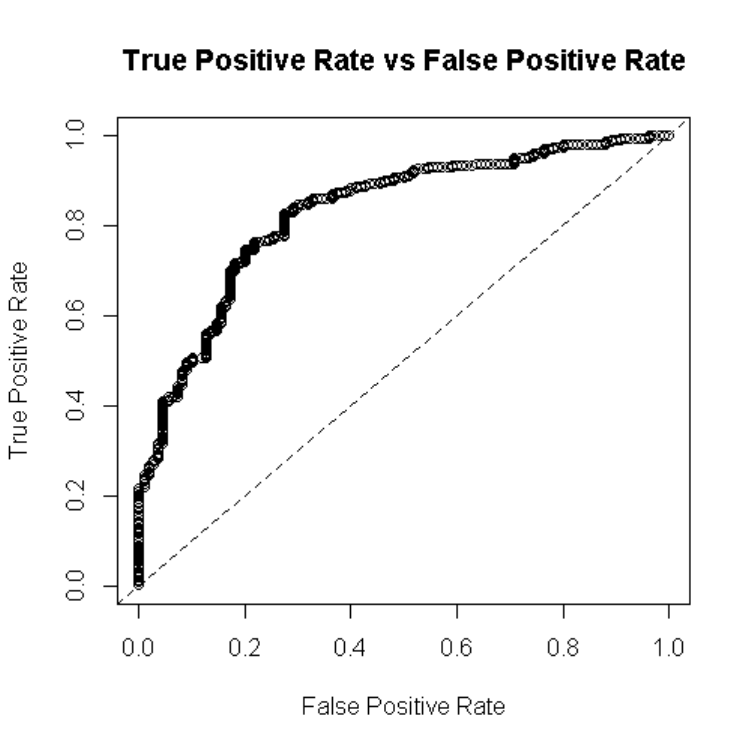
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
Figure 4. Area Under the Curve for the Gradient Boosting Machine When Differentiating Confirmed
Pure Financial Exploitation from Confirmed Hybrid Financial Exploitation
Figure 4: The percent correctly classified by chance is 78.09%. This prediction improved to
83.06% using the GBM algorithm.
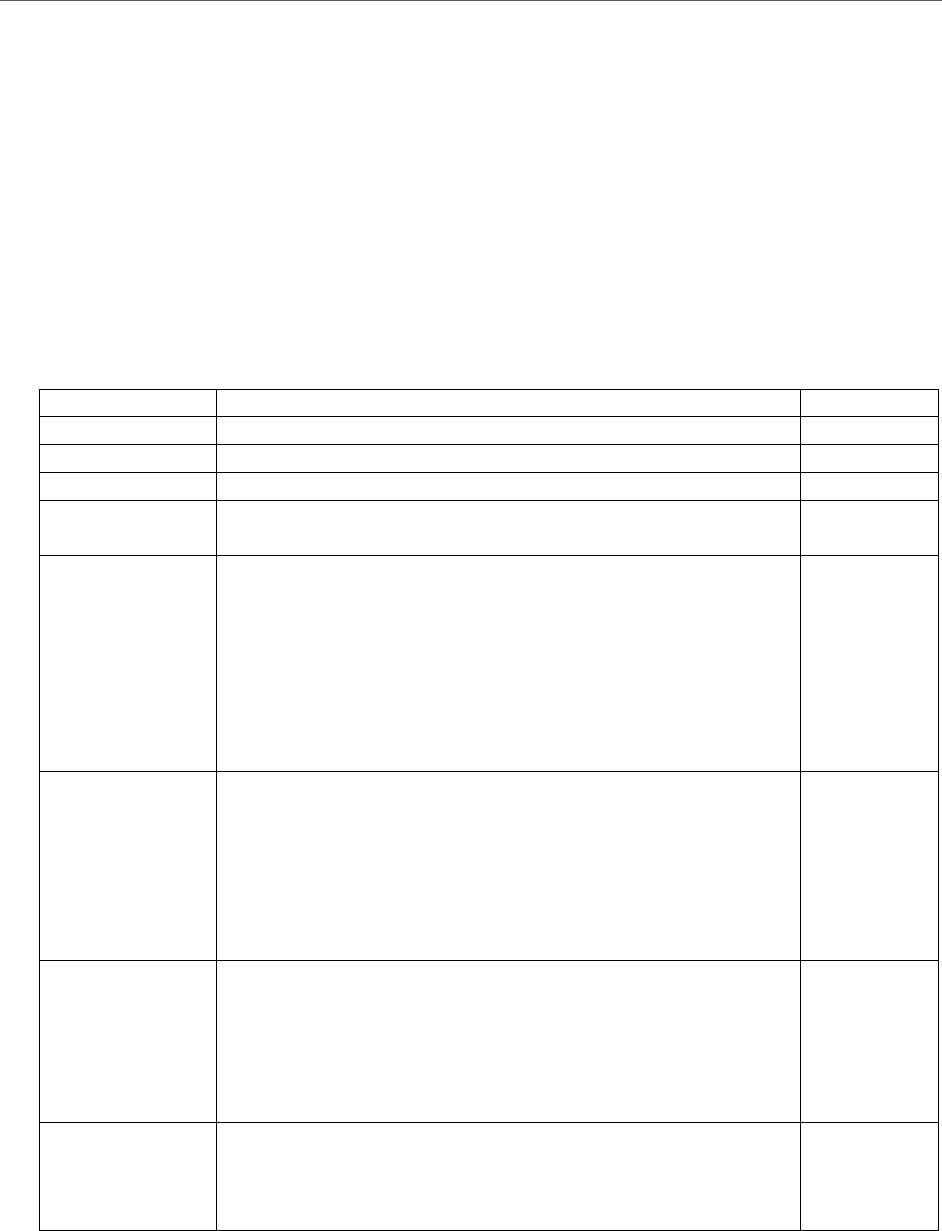
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
SELF-NEGLECT ABUSE TYPES
In original APS report, there are 8 defined types of abuse:
EMOTIONAL ABUSE
EXPLOITATION
MEDICAL NEGLECT
MENTAL HEALTH NEGLECT
PHYSICAL ABUSE
PHYSICAL NEGLECT
SUICIDAL THREAT
SEXUAL ABUSE
Table 1 The following variables are for victims: victim demographics, victim characteristics, CARE tool variables. There are two
race/ethnicity variables: “eth_6” is a 6-category variable while “eth_alt” is 4-category.
Variable
Coding
Type(length)
stage
Unique stage ID
Num(8)
id
Unique person ID for victims
Num(8)
gend
12 9
Char(1)
age
Age in years (group into 5 year range)
0--
Num(3)
eth_6
Ethnicity (6 category) in APS DRIT 72101
Char(1)
eth_alt
Alternative HHSC grouping (derived from 6 race/ethnicity
indicators in APS DRIT 70717)
Char(1)
living
Categorical variable for living arrangement:
Char(1)
marital
Categorical variable for Marital status:
Char(1)
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
parated
*clnt1 - 23
Client Characteristics for victims
Char(1)
*care1 - 57
Char(1)
Unavail_street
Char(1)
*zcomm1-44
Geocoded community level variables (zip resolution)
Num(8)
*tcomm1-44
Geocoded community level (census tract resolution)
Num(8)
*See attached list for numbered variables.
1 CODING OF VARIABLES RELATED TO ABUSE TYPES (APPLIES TO
“VICTIM_ROWS”, “VIC_PERP_PAIR”, “VIC_FIRST_STAGE”)
Table 2 Summary of abuse information for a victim
Variable
Coding
Type(length)
any_cfm
Char(1)
any_uncfm
Any un-
Char(1)
any_cfm_sn
Any confirmed self-neglect
Char(1)
any_uncfm_sn
Any un-confirmed self-neglect
Char(1)
*Ind_cfm1-11
Indicator for confirmed abuse types per victim
Char(1)
*Ind_uncfm1-11
Indicator for unconfirmed abuse types per victim
Char(1)
fe
Per Case FE status: (P)ure FE, (H)ybrid FE, (O)ther or (N)one
Char(1)
*See attached list for numbered variables.
2 CODING OF VARIABLES RELATED TO PERPETRATORS (APPLIES TO
“PERP_ROWS”, “VIC_PERP_PAIR”)
Table 3 The following variables are for perpetrators: self-indicator, role, relationship to corresponding victim, demographics,
characteristics, abuse types (confirmed), abuse types (unconfirmed).
Variable
Coding
Type(Length)
self
Is perpetrator self to victim
Char(1)
p_role
Role of the perpetrator:
char(2)
p_rel
The the victim:
char(1)
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
than
family member.
p_orig_rel
Char(30)
p_id
Unique person ID for perpetrators
Num(8)
p_gend
Perpetrator gender12 9
Char(1)
p_age
Perpetrator age in years
Num(3)
p_eth_6
Perpetrator ethnicity (same format as victims)
Char(1)
p_eth_alt
Perpetrator alternative ethnicity (same format as victims)
Char(1)
p_living
Perpetrator living arrangement(same format as victims)
Char(1)
p_marital
Perpetrator marital status (same format as victims)
Char(1)
*p_clnt1 – 22
Perpetrator characteristics (same format as victims)
Char(1)
*type_cfm1– 8
;
type
Char(1)
*type_uncfm1 –8
;
type
Char(1)
P_fe
Per perpetrator FE status: (P)ure FE, (H)ybrid FE, (O)ther or
(N)one
Char(1)
*See attached list for numbered variables.
3 OTHER VARIABLES
Table 4 Other variables
Variable
Coding
Type(length)
episode
Stage sequence # for a victim; counting from his/her first
stage in APS report
Num(3)
FY
APS fiscal year
Num(3)
4 LIST OF NUMBERED VARIABLES
4.1 CLIENT CHARACTERISTICS (CLNT1-23)
1. AGED: age >=65 (should be ‘Y’ for all victims))
2. ALCOHOL ABUSE
3. AUTISM
4. CI: Cognitively Impaired
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
5. DDD: Developmental Disability-Diagnosed
6. DRUG ABUSE
7. HEARING IMPAIRED
8. HIV AIDS
9. IDD: Intellectual and Developmental Disability
10. LIMITED ENGLISH
11. MDCP CLASS: Receiving MDCP/CLASS
12. MW HCS: Medicaid Waiver: Receiving HCS Services
13. MW WL: Medicaid Waiver: Waiting List
14. MENTAL ILLNESS
15. MILITARY DEPENDENT
16. MOBILITY IMPAIRED
17. PHYSICALLY DISABLED
18. SPEECH DISABLED
19. VISUALLY IMPAIRED
20. UNDETERMINED IMMIGRATION STATUS
21. UNQUALIFIED IMMIGRANT
22. PERMANENT RESIDENT
23. US CITIZENSHIP
4.2 CONFIRMED ABUSE TYPE (TYPE_CFM1 –8), UNCONFIRMED ABUSE TYPE
(TYPE_UNCFM1 –8)
1. EMOTIONAL ABUSE
2. EXPLOITATION
3. MEDICAL NEGLECT
4. MENTAL HEALTH NEGLECT
5. PHYSICAL ABUSE
6. PHYSICAL NEGLECT
7. SUICIDAL THREAT
8. SEXUAL ABUSE
4.3 SUMMARY INDICATOR OF CONFIRMED ABUSE TYPE (IND_CFM1-11), SUMMARY
INDICATOR OF UNCONFIRMED ABUSE TYPE
(IND_UNCFM1-11)
1. EMOTIONAL ABUSE
2. EXPLOITATION
3. MEDICAL NEGLECT (by caregiver)
4. MENTAL HEALTH NEGLECT (by caregiver)
5. PHYSICAL ABUSE
6. PHYSICAL NEGLECT (by caregiver)
7. SUICIDAL THREAT
8. SEXUAL ABUSE
9. MEDICAL NEGLECT (by self)

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
10. MENTAL HEALTH NEGLECT (by self)
11. PHYSICAL NEGLECT (by self)
4.4 CARE VARIABLES (CARE1-57)
See variable list in attached CARE document (link).
4.5 COMMUNITY LEVEL VARIABLES (TCOMM1-44, ZCOMM1-44)
Variables with name starting with U.S. census tract; variables with name starting
1. Total population
2. Total male population
3. Total female population
4. Percent 60 years and older
5. Percent 60 years and older (male)
6. Percent 60 years and older (female)
7. Percent 65 years and older
8. Percent 65 years and older (male)
9. Percent 65 years and older (female)
10. Percent 75 years and older
11. Percent 75 years and older (male)
12. Percent 75 years and older (female)
13. Median age
14. Median age (male)
15. Median age (female)
16. Total Non-Hispanic White
17. Total Non-Hispanic Black
18. Total Non-Hispanic American Indian & Alaskan Native
19. Total Non-Hispanic Asian
20. Total Non-Hispanic Native Hawaiian & Other Pacific Islanders
21. Total Non-Hispanic Other Race
22. Total Non-Hispanic Multiple Races (2 or more)
23. Total Hispanic
24. Percent in poverty
25. Percent in poverty (65 years and older)
26. Households
27. Households receiving Food Stamps
28. Households receiving Social Security
29. Households receiving Supplemental Security Income
This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
30. Total Foreign-born
31. Total Foreign-born / Naturalized Citizens
32. Total disabled
33. Total 65 and older
34. Total 65 and older with disability
35. Total 65 and older with hearing difficulties
36. Total 65 and older with vision difficulties
37. Total 65 and older with cognitive difficulties
38. Total 65 and older with ambulatory difficulties
39. Total 65 and older with self-care difficulties
40. Total 65 and older with independent living difficulties
41. Total unemployed (16 and over population)
42. Total population 25 years and older
43. Percent with high school degree or equivalent (25 years and older)
44. Percent with degree (25 years and older)

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.

This resource was prepared by the author(s) using Federal funds provided by the U.S.
Department of Justice. Opinions or points of view expressed are those of the author(s) and do not
necessarily reflect the official position or policies of the U.S. Department of Justice.
